
0x00 前言
最近Cloudflare有一些新动作,再加上一些可用的优选IP,大带宽节点,这不就是一个完美的图片CDN吗?之前白嫖的CDN虽然也行,但是节点偏少,并且节点带宽仅为10M,图片较大的话,网站的加载体验感就不是很好。说干就干,直接开始!
0x01 寻找优选IP
推荐选择TCP延迟较低,并且带宽较大的节点,这里我推荐一个默认和移动解析
| 默认 | *.cloudflare.182682.xyz. |
| 移动 | digitalocean.com |
还有一些其他的CloudFlare公共Cname域名,注意甄别
| 地址名称 | 协议版本 | 维护周期 | 备注说明 |
|---|---|---|---|
| *.cloudflare.182682.xyz | 4&6 | 15ip/15分钟 | 泛域名解析可以解析到任意前缀,本站提供维护 |
| bestcf.top | 4 | 24H | VPS789 |
| cdn.2020111.xyz | 4 | 15ip/10分钟 | 网络收集 |
| cfip.cfcdn.vip | 4 | 6ip/1天 | 网络收集 |
| cf.0sm.com | 4&6 | 手动更新 | 网络收集 |
| cf.090227.xyz | 4&6 | 未知频率 | 网络收集 |
| cf.zhetengsha.eu.org | 4 | 未知频率 | 网络收集 |
| cloudflare.9jy.cc | 4 | 未知频率 | 网络收集 |
| cf.zerone-cdn.pp.ua | 4 | 未知频率 | 网络收集 |
| cfip.1323123.xyz | 4 | 未知频率 | 网络收集 |
| cnamefuckxxs.yuchen.icu | 4 | 未知频率 | 网络收集 |
| cfip.xxxxxxxx.tk | 4 | 未知频率 | OTC大佬提供维护 |
| cloudflare-ip.mofashi.ltd | 4 | 未知频率 | 网络收集 |
| 115155.xyz | 4&6 | 18ip/1小时 | 网络收集 |
| cname.xirancdn.us | 4&6 | 未知频率 | 网络收集 |
| f3058171cad.002404.xyz | 4&6 | 未知频率 | 网络收集 |
| speed.marisalnc.com | 4 | 1000ip/3分钟 | 【推荐】ktff大佬提供维护 |
| 8.889288.xyz | 4 | 未知频率 | 网络收集 |
| cdn.tzpro.xyz | 4 | 未知频率 | 网络收集 |
| cf.877771.xyz | 4 | 未知频率 | 网络收集 |
| xn--b6gac.eu.org | 4 | 未知频率 | ↗↘↗.eu.org |
| freeyx.cloudflare88.eu.org | 4 | 1000ip/3分钟 | 同speed.marisalnc.com |
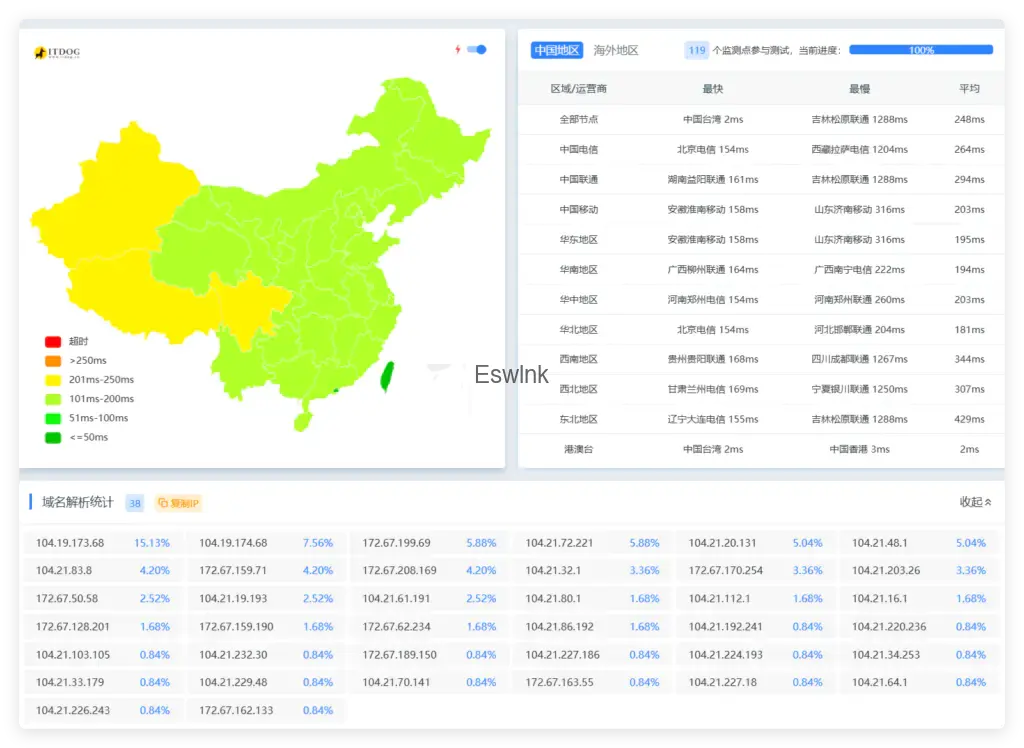
尽量保证三网线路的解析不会超时,如下图所示:
0x02 Cloudflare 相关设置
由于Cloudflare的免费版本不能在Origin Rules里修改相关的SNI设置,所以不能实现绕过备案,所以这里我推荐其他的相关配置(当然你可以尝试使用workers来实现,不过cf的免费版本每天支持10w次请求)
Cache Rules
边缘TTL直接设置1年,并且忽略查询字符串,如果要实现相关的裁剪,在bucket的设置相关的接口,切记不要使用「?」作为样式分隔符,如果可以的话,建议开启原始资源保护,保证你的每个图片都有自己的相关水印。
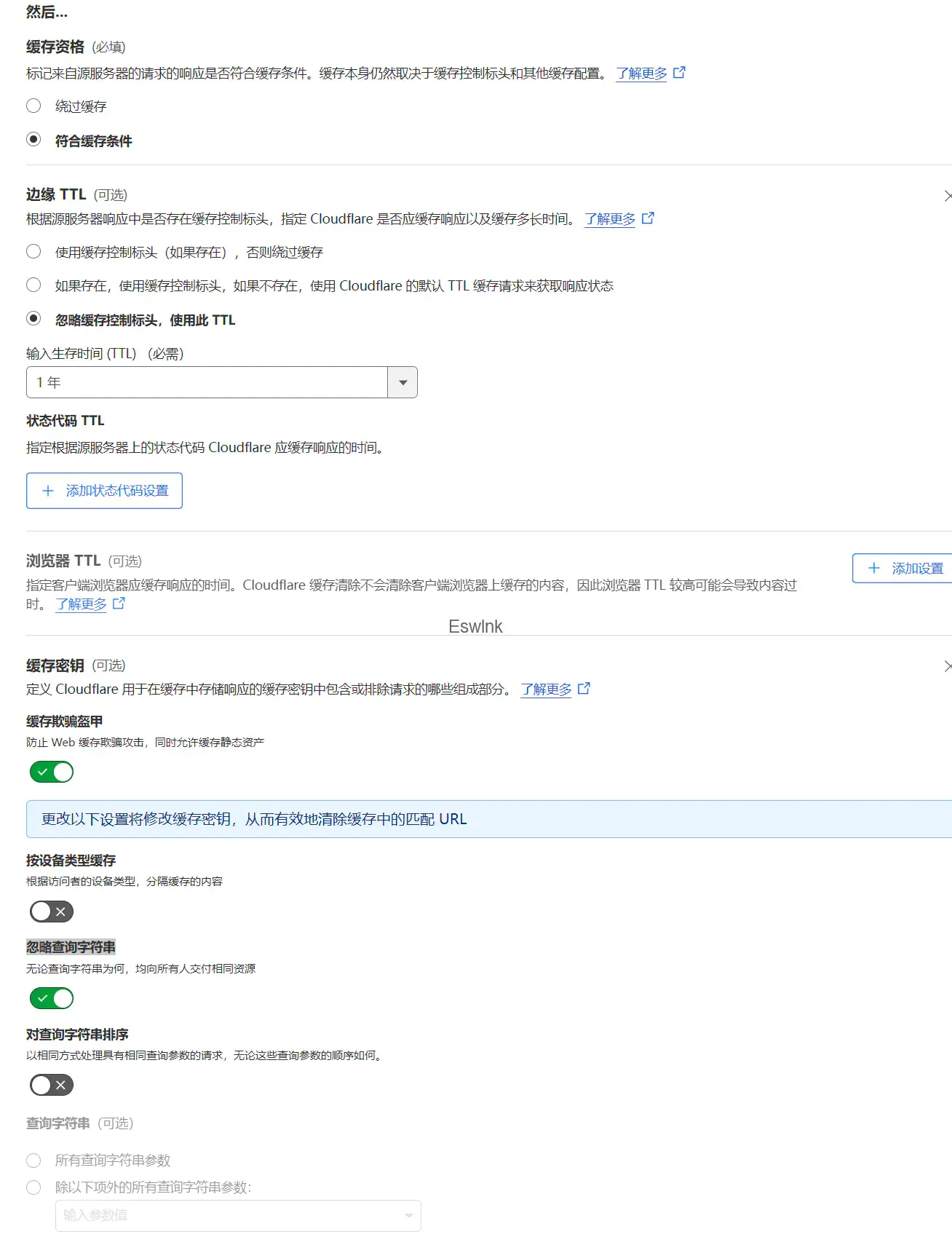
这里的状态代码TTL可以根据相关bucket厂商是否对403或者404状态计算回源流量来进行缓存,如果你像我一样,只是单纯的用作图片CDN,那么全缓存没有问题,当然这也会导致一个问题:当一位攻击者掌握你的图片命名逻辑时,可能会导致你的上传的新图片被404状态码覆盖。
WAF配置
此步骤可以省略,最开始是想要来防止被采集图片,但是苦于Cloudflare不能像Edgeone一样校验鉴权设置,只有在Workers上进行设置,所以就随便用点规则。
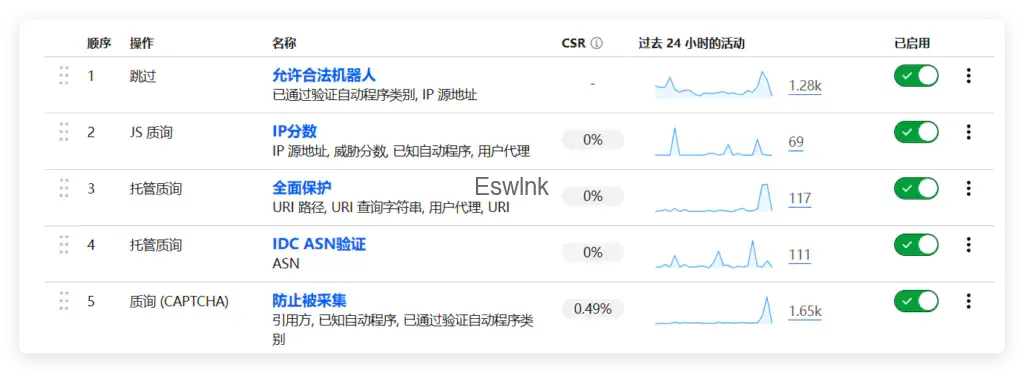
允许合法机器人
(cf.verified_bot_category in {"Search Engine Crawler" "Search Engine Optimization" "Monitoring & Analytics" "Page Preview"}) or (ip.src eq ******) or (ip.src in {110.249.201.0/24 110.249.202.0/24 111.225.148.0/24 111.225.149.0/24 220.243.135.0/24 220.243.136.0/24 220.243.188.0/24 220.243.189.0/24 60.8.123.0/24 60.8.151.0/24})IP分数
(ip.src in $block) or (cf.threat_score gt 10 and not cf.client.bot) or (http.user_agent contains "Pixalate.com/1.0") or (http.user_agent contains "python-requests") or (http.user_agent contains "MJ12bot") or (http.user_agent contains "PetalBot")Block托管的列表IP基本没啥用,网上随便找找,保证正常蜘蛛能够爬取即可
相关保护
(http.request.uri.path contains "../..") or (http.request.uri.path contains "/*") or (http.request.uri.path contains "etc/passwd") or (http.request.uri.query contains "gopher:") or (http.request.uri.query contains "doc:") or (http.request.uri.query contains "php:") or (http.request.uri.query contains "glob:") or (http.request.uri.query contains "file:") or (http.request.uri.query contains "phar:") or (http.request.uri.query contains "zlib:") or (http.request.uri.query contains "ftp:") or (http.request.uri.query contains "ldap:") or (http.request.uri.query contains "dict:") or (http.request.uri.query contains "ogg:") or (http.request.uri.query contains "data:") or (http.request.uri.query contains ":$") or (http.request.uri.query contains "${") or (http.request.uri.query contains "invokefunction") or (http.request.uri.query contains "call_user_func_array") or (http.request.uri.query contains "\\think\\") or (http.request.uri.query contains "base64_decode(") or (http.request.uri.query contains "define(") or (http.request.uri.query contains "eval(") or (http.request.uri.query contains "file_get_contents(") or (http.request.uri.query contains "include(") or (http.request.uri.query contains "require(") or (http.request.uri.query contains "require_once(") or (http.request.uri.query contains "shell_exec(") or (http.request.uri.query contains "phpinfo(") or (http.request.uri.query contains "system(") or (http.request.uri.query contains "passthru(") or (http.request.uri.query contains "char(") or (http.request.uri.query contains "chr(") or (http.request.uri.query contains "preg_") or (http.request.uri.query contains "execute(") or (http.request.uri.query contains "echo(") or (http.request.uri.query contains "print(") or (http.request.uri.query contains "print_r(") or (http.request.uri.query contains "var_dump(") or (http.request.uri.query contains "fopen(") or (http.request.uri.query contains "alert(") or (http.request.uri.query contains "showmodaldialog(") or (http.request.uri.query contains "$_GET[") or (http.request.uri.query contains "$_POST[") or (http.request.uri.query contains "$_COOKIE[") or (http.request.uri.query contains "$_FILES[") or (http.request.uri.query contains "$_SESSION[") or (http.request.uri.query contains "$_ENV[") or (http.request.uri.query contains "$_PHPLIB[") or (http.request.uri.query contains "$_GLOBALS[") or (http.request.uri.query contains "$_SERVER[") or (http.user_agent contains "mj12bot.com") or (http.user_agent contains "censys") or (http.user_agent contains "Go-http-client") or (http.request.uri contains ".asp") or (http.request.uri contains ".aspx") or (http.user_agent contains "msray-plus") or (http.request.uri contains ".ashx") or (http.user_agent contains "Skywork") or (http.user_agent contains "GPTBot") or (http.user_agent contains "DataForSeoBot") or (http.user_agent contains "mj12bot.com") or (http.request.uri.query contains " or ") or (http.request.uri.query contains " xor ") or (http.request.uri.query contains " and ") or (http.request.uri.query contains " =") or (http.request.uri.query contains " <") or (http.request.uri.query contains " >") or (http.request.uri.query contains "'") or (http.request.uri.query contains "current_user")这一规则主要使用来防止扫描或者SQL注入的,如果你并没有使用厂商的bucket,而是选择了自己的主机或者服务器,那么这个规则也许能够帮上一些忙,不过基本没用
IDC ASN验证
(ip.geoip.asnum in {14618 16509 8075 4766 25532 64022 134768 22362})防止低端采集
(not http.referer contains "eswlnk.com") or (cf.client.bot and not cf.verified_bot_category in {"Search Engine Crawler" "Search Engine Optimization" "Monitoring & Analytics" "Academic Research" "Page Preview"})像这种,加个referer就能够直接采集到你的图片,如果想要尽可能防止大规模采集,可以采用时间戳验证和token校验,一般大厂bucket都支持。
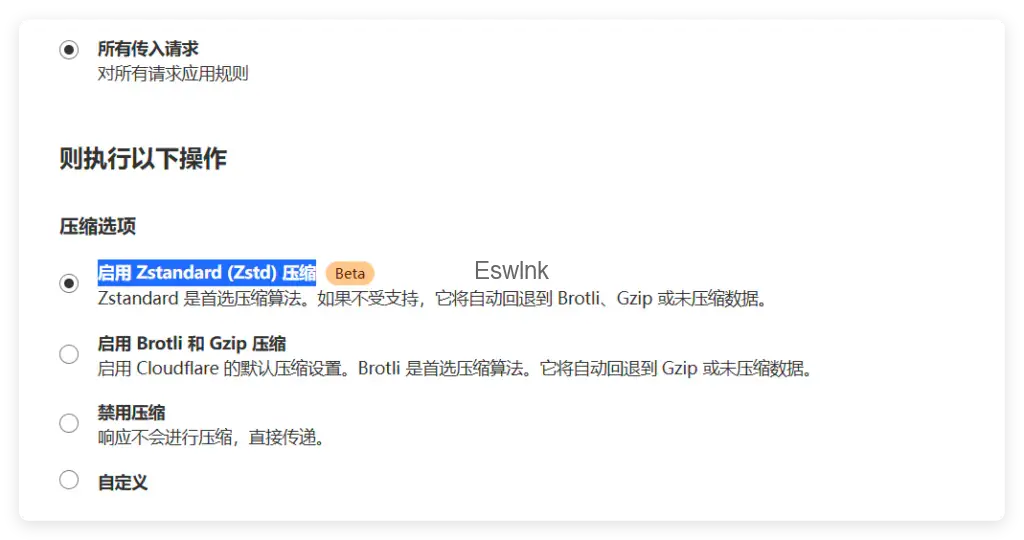
Compression Rules
以图片文件CDN为例,对所有传入请求进行压缩处理,并启用 Zstandard (Zstd) 压缩
0x03 效果测试
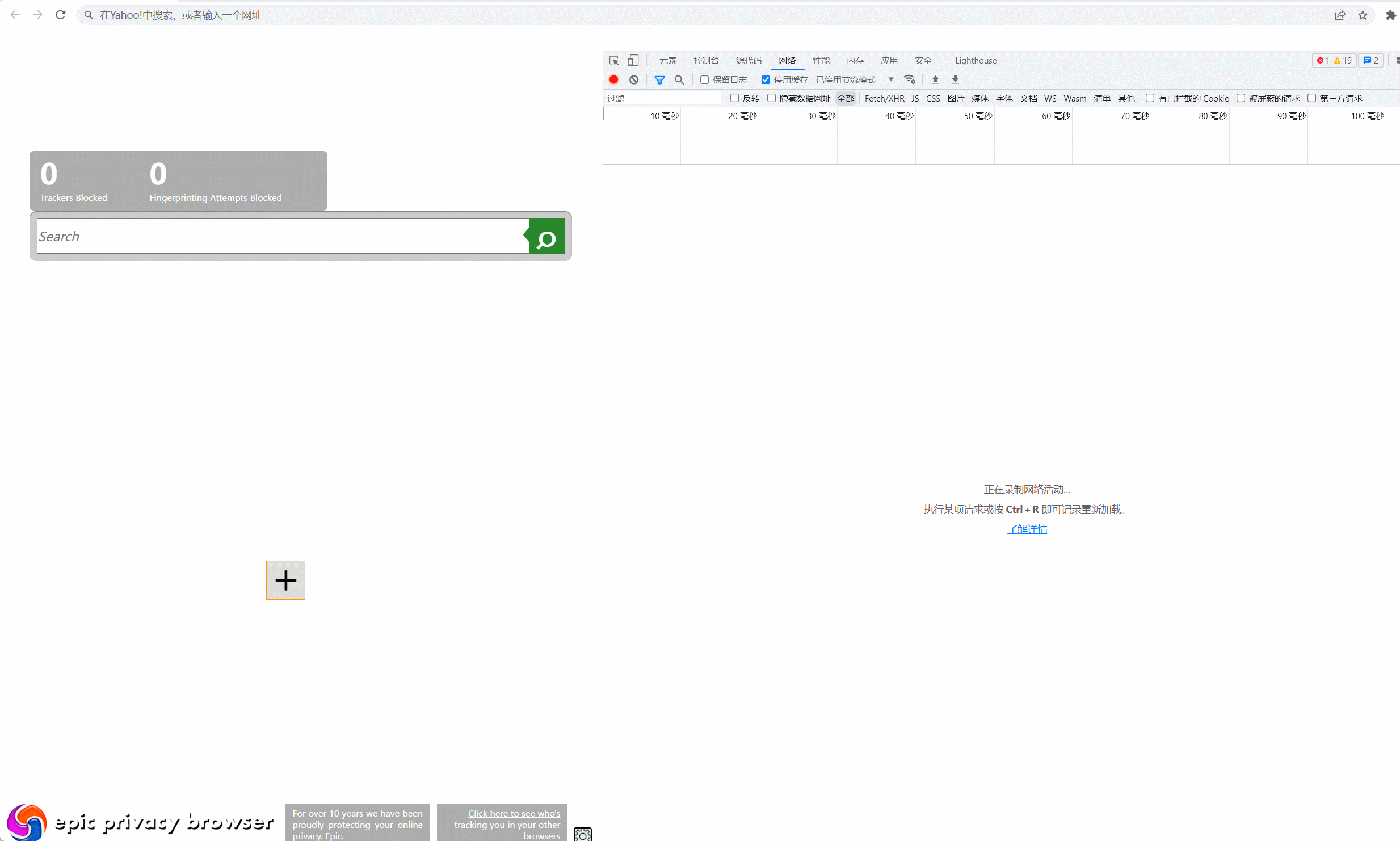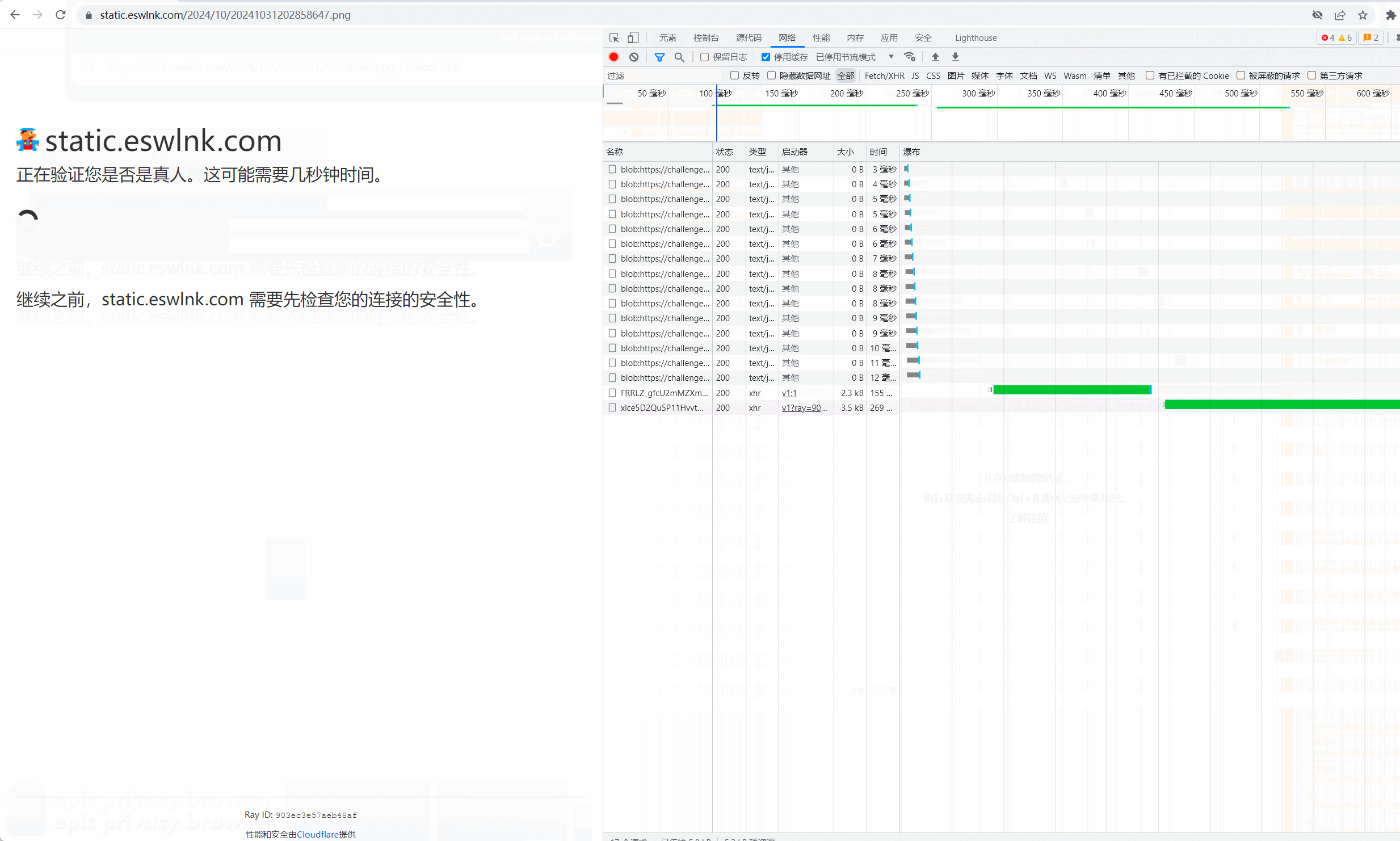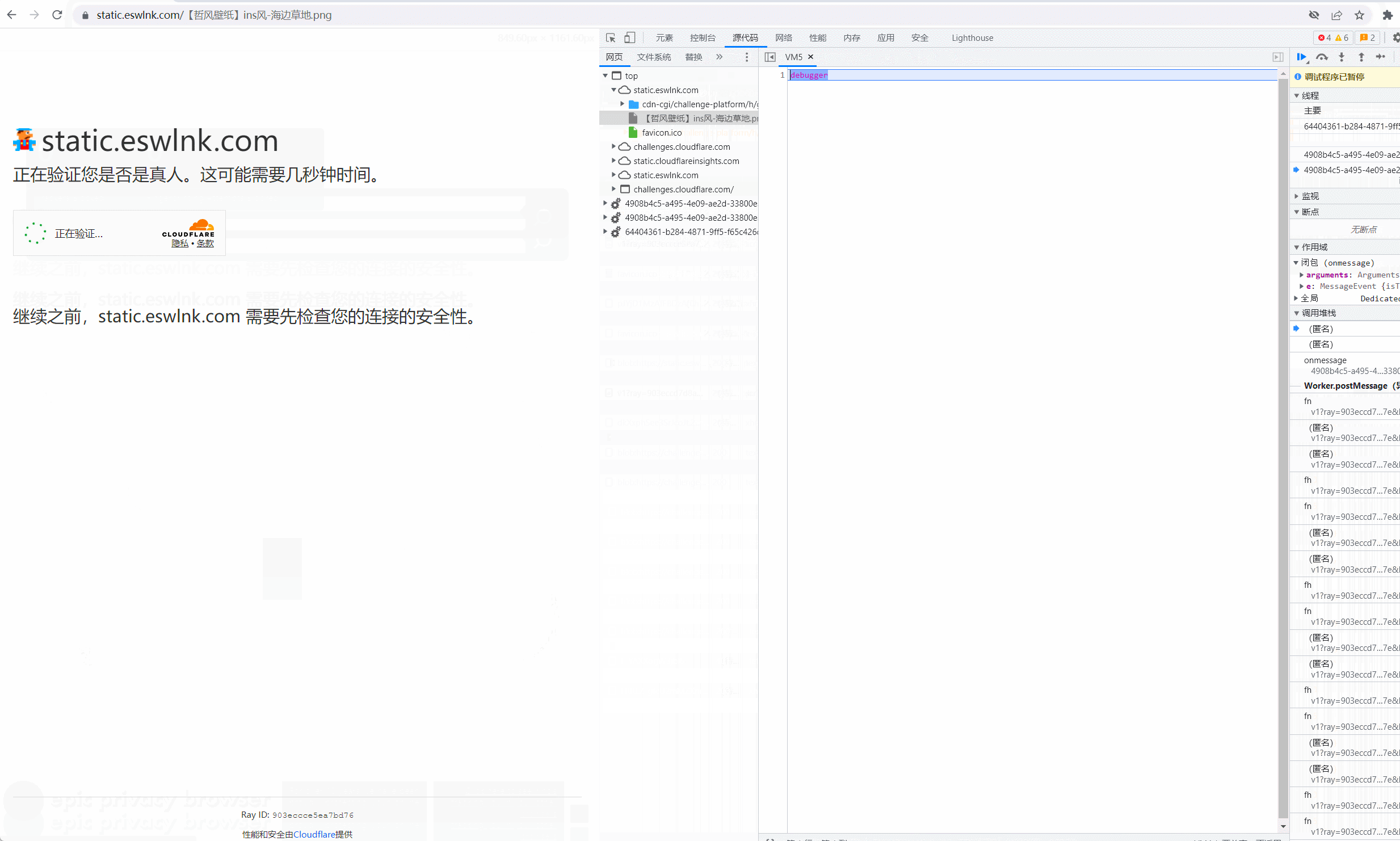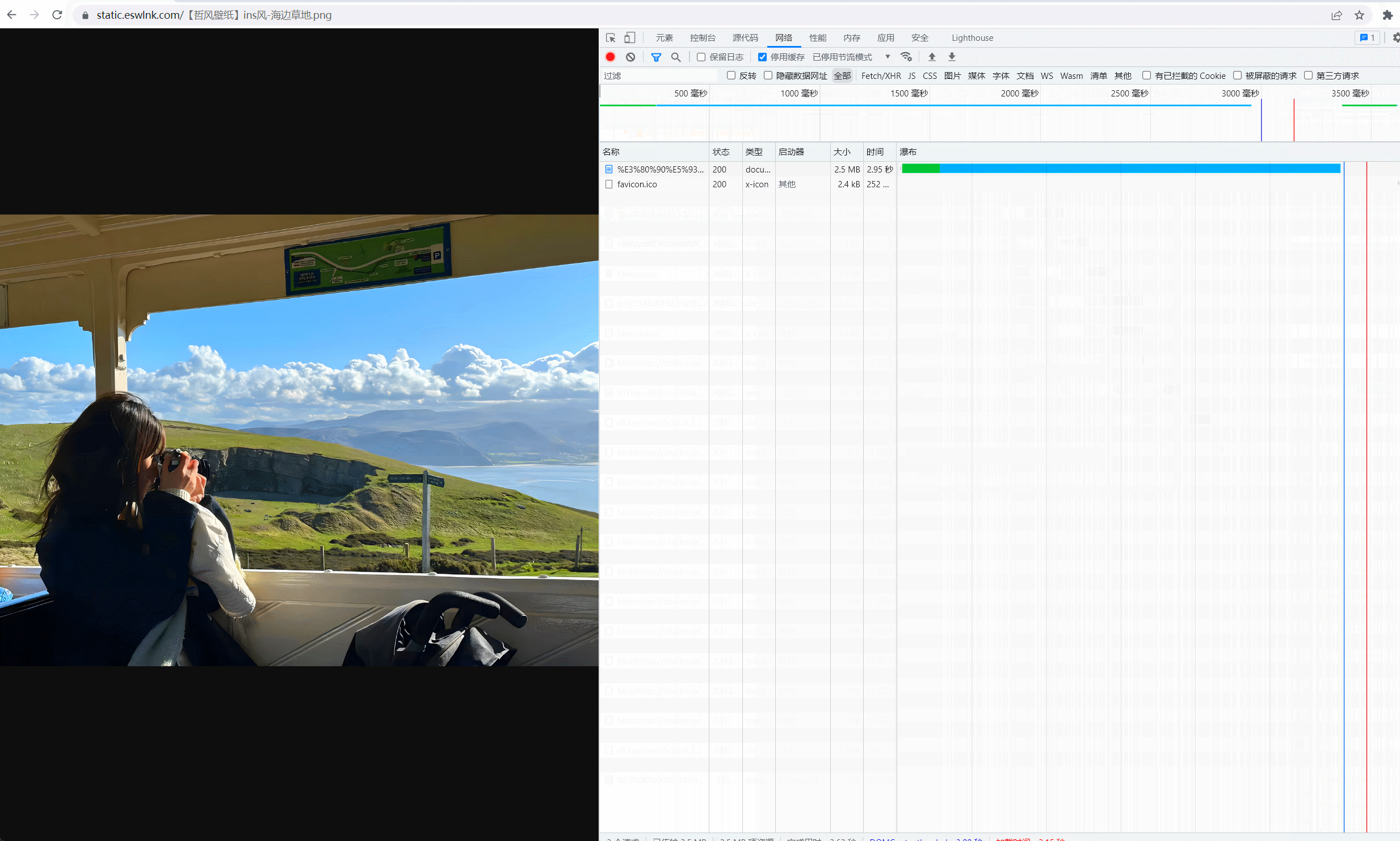
0x04 Workers可用Token校验
提供一份简单的代码,自己手搓一个插件实现相关功能即可:
addEventListener('fetch', event => {
event.respondWith(handleRequest(event.request));
});
async function handleRequest(request) {
const url = new URL(request.url);
const token = url.searchParams.get('token');
const resourcePath = url.pathname;
// 验证 Token
if (!validateToken(resourcePath, token)) {
return new Response('Access Denied', { status: 403 });
}
// 允许访问资源
return fetch(request);
}
function validateToken(resourcePath, token) {
const SECRET_KEY = 'your_secret_key';
const [timestamp, signature] = token.split(':');
// 检查 Token 是否过期
if (Date.now() / 1000 > parseInt(timestamp)) {
return false;
}
// 重新计算签名
const message = `${resourcePath}:${timestamp}`;
const expectedSignature = CryptoJS.HmacSHA256(message, SECRET_KEY).toString();
// 比较签名
return signature === expectedSignature;
}




评论 (0)